Bitcoins at heart of server breach, ISU offers identity protection service
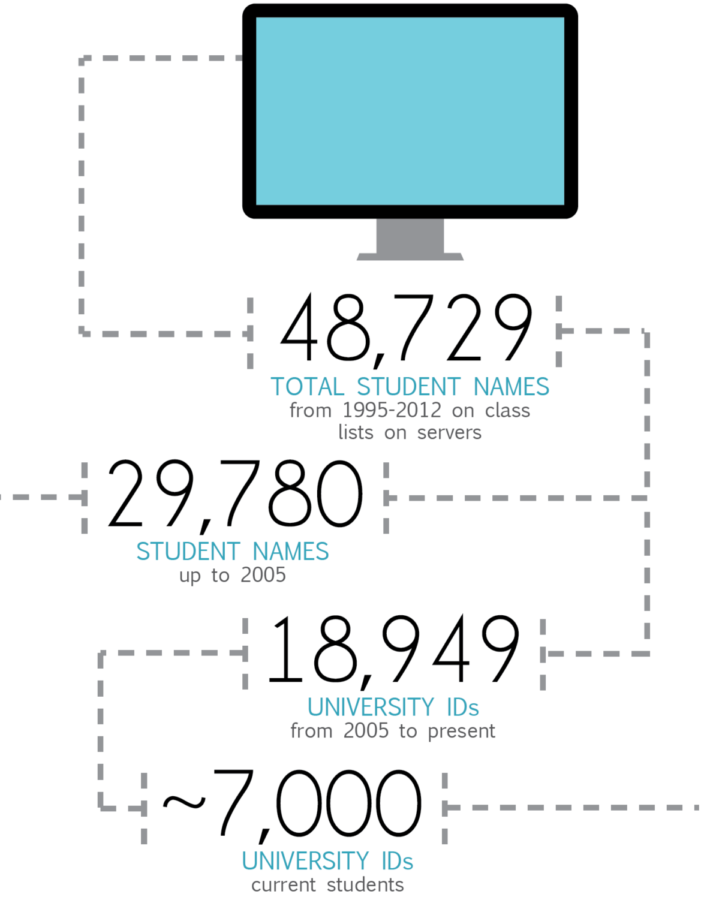
From 48,729 of the total student names, 29,780 were students from 1995 to 2005. The other 18,949 were student IDs from 2005 to the present, and 7,000 of those are current students.
April 22, 2014
Over 29,000 students enrolled between 1995 and 2012 may have had their Social Security numbers compromised due to a security breach affecting five departmental servers on campus.
Officials said they believe the hackers that breached five campus network servers were using computers to generate bitcoins.
Jonathan Wickert, senior vice president and provost, said the IT department discovered software on the servers that was uploaded by hackers. The servers are network-attached storage devices, which Wickert described as a special kind of computer.
“What we found is that we had some computers on campus that were doing unusually large amount of computing. They were extra busy,” Wickert said.
The software loaded onto the servers were part of a process called bitcoin mining, Wickert said. Bitcoins are generated as a reward for users who offer computing power and record payments in a public ledger. The bitcoins are then created as a digital form of money that can be exchanged for merchandise anonymously.
“These criminals broke into a couple of our computers and wanted to use our computers for their calculations. By using our computers and other computers around the world, they could have many computers all at once doing these calculations,” Wickert said.
The university discovered the breach February 28 and repaired the networks over the weekend so they were again secure March 3, Wickert said. No data files or financial information was breached.
“At that point, we put together a team of people on campus: campus police, IT, my office. We then began scanning the entire network, all 100,000 devices connected to our network,” Wickert said. “We removed the computers that were infected, took them offline. We actually deleted the files and destroyed those particular computers because we knew they were vulnerable.”
Wickert said it was not until an analysis was completed March 17 that they determined that three out of the five servers contained class lists from 1995 to 2012, which is an issue because Social Security numbers were used as university IDs up until 2005.
Some compromised servers contained Social Security numbers of students who took a class in computer science from 1995 to 2005. Numbers of students enrolled in world languages and cultures from 2004, 2007 and 2011 to 2012 may also be compromised.
The university ID numbers are paired with a password and are only useable on-campus, so Wickert said those numbers are not of as high of an importance.
“We have no evidence that the class lists were viewed. We have no evidence that the class lists were downloaded. We think what these hackers were doing is they wanted to have these computers do all these bitcoin calculations,” Wickert said. “So we have no evidence that they accessed those class lists, but we’re just being cautious and notifying everybody.”
An email and a hard-copy letter have been sent out to current students at the address listed for them on AccessPlus. Students enrolled from 1995 to 2012 whose Social Security number or password may be compromised are being notified through a letter in the mail, as well.
The university will provide a free year of credit and identity monitoring for former students with compromised Social Security numbers by AllClear, a firm specializing in computer security breaches.
“They’re providing the identity protection service, the credit monitoring service,” Wickert said. “They’ll have a call center that’s staffed to answer questions, and really they’re just able to provide a high level of service.”
Wickert said the five infected servers have been destroyed and are planning to make passwords across the university stronger. Encrypting all university laptops and using a type of software that can identify where personal information is stored on a network are also among the proactive plans the university and IT will implement.
Synology, the company that designed the five hacked servers, is vulnerable to hacking, and similar instances with Synology servers have occurred around the globe, Wickert said.
“Not all computers are amenable to being hacked into like this, but this particular model, they figured out how to break into that one,” Wickert said. “This is a global problem, and it’s difficult to chase these suspects down.”
Wickert said the IT department defends against dozens of possible breaches a day.
“This was one that got through. What we want to do is learn from it and get better at it,” Wickert said.