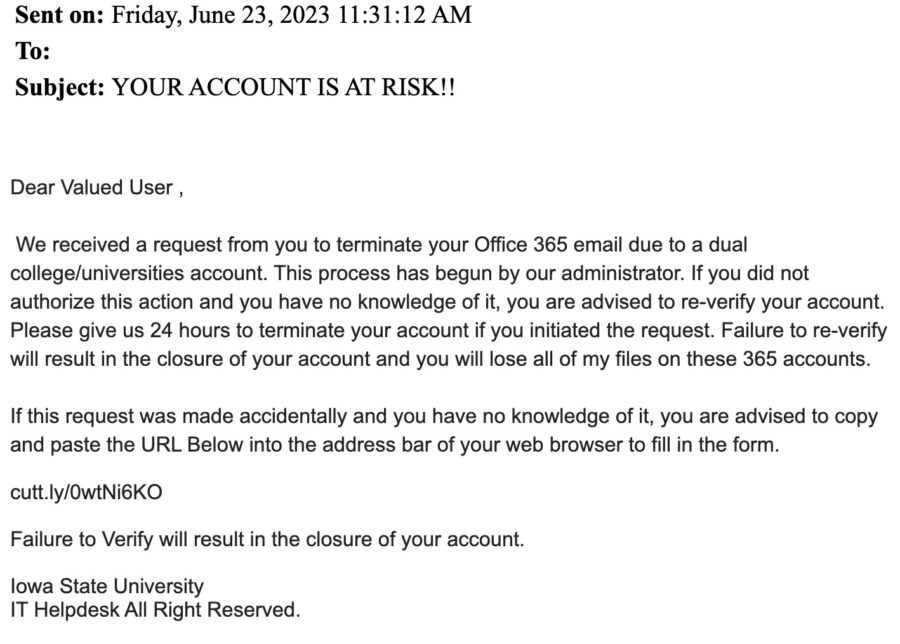
“YOUR ACCOUNT IS AT RISK,” email phishing scam targets Iowa State
An email of the recent phishing scam threatening termination of the user’s Office 365 account
Iowa State students and faculty have been targeted with phishing scam emails which Rich Tener, the university’s chief information security officer, said have been “very very persistent” over the last two to three weeks.
Recent phishing examples initially began with emails informing the recipient that their Office 365 account will be shut down if it is not reverified through a TinyURL, which Iowa State would never send out, said Doug Jacobson, professor of electrical and computer engineering.
“Nobody who has your information is going to send you an email asking for your information,” Jacobson said. “Things like [Office 365 accounts] don’t get terminated with emails and links and asking for information; that’s just that’s not how things are operated”
Tener said that in this case, the scammer initially asked for login information and a phone number for the account. Then they will impersonate the IT help desk and ask them to send the next multi-factor authentication code they receive.
“The attackers or the scammers go one step further and they text the student directly saying, ‘Hey, this is the IT department. We need you to verify your account. Send us the next security code you receive,’” Tener said.
Once they have that information, Tener said they can log in and then send ten thousand new phishing emails per account they gain access to. They also implement a rule in Microsoft Office to automatically delete any incoming email, so any good samaritan message warning the user that someone else has access to their account will not be received.
“Then finally, once they have enough of [email accounts], they use it to send out the job scam,” Tener said. “So it’s like a multi-phase attack where they’re phishing, phishing, and then they launched their end game, which is job scam.”
The second phase of this scam sends a different type of email informing the recipient of a job offer Jacobson said was “too good to be true.”
“Things that are too good to be true [and] things that have an enormous sense of urgency or something bad happens, those are things that you really kind of need to be really leery of,” Jacobson said.
Ultimately, after someone “applied” and was “employed,” Tener said they would receive a fraudulent check and be asked to send gift cards to their new “employer.”
“You think, ‘Oh, well, I’ve got money in my account, I can totally go ahead and do that,’ but the check bounces and when your bank finds out they take all the money away,” Tener said. “So, anything that you’ve spent or given to the scammer, you’ve lost.”
Jacobson was able to track the domain of the recent phishing emails to Montenegro.
“Montenegro is the domain, but it just goes to a hosting site,” Jacobson said. “So, anybody can just buy something, and usually they’ll do it in countries whose internet laws aren’t as robust and so therefore less likely.”
Tener said once they identify that an email is a phishing scam they delete it from any Iowa State associated inbox that received it.
“So we kick the attacker out, we remediate the problem and then we try to delete the email from everyone’s inbox as fast as we can,” Tener said. “But unfortunately, they still get delivered before we can get them out.”
Tener said he could not quantify the number of emails impacted but said it is “definitely more than a handful.”
“Be vigilant about a job offer,” Tener said. “If you haven’t met your employer, you probably shouldn’t be taking money from them, and you shouldn’t be using your own personal bank account to buy things for someone else or for your employer.”
A recipient of a fishy email can report it in Outlook, which sends it to Tener’s team, or forward the email to [email protected]. Someone who believes their account has been accessed by someone else can email the solutions desk at [email protected].
Ultimately, Tener said that the university will never deactivate an account of a currently enrolled student and it is imperative to keep account information private.
“We’ll never ask you for your password, and no employee will ever ask you for your password,” Tener said. “We’ll never approach you over SMS and ask you for your security code. You should never give that to anyone.”
Your donation will support the student journalists of the Iowa State Daily. Your contribution will allow us to purchase equipment, send our student journalists to conferences and off-set their cost of living so they can continue to do best-in-the-nation work at the Iowa State Daily.