IT Services offers tips on how to combat CryptoLocker virus
Graphic: Azwan Azhar/ Iowa State Daily
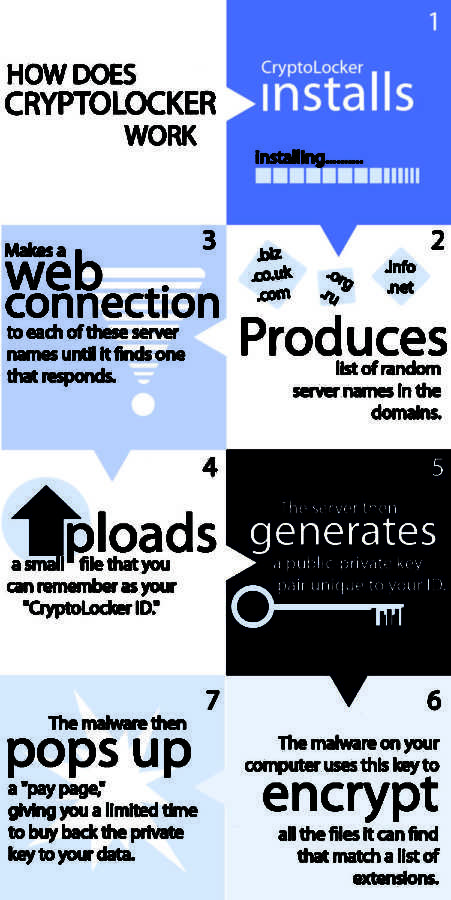
Theses are the steps on how CryptoLocker works. Information was derived from http://nakedsecurity.sophos.com.
October 30, 2013
The CryptoLocker virus that Iowa State’s Information Technology Services has been dealing with has reared its head for five ISU students.
The virus, once put on a Windows PC via an email attachment or website, locates and grabs hold of the user’s files. Through a process that searches for the best available way to keep hold of the files, the encrypted files are linked through the web to whichever server the virus finds to be adequate.
From there, a message pops up describing what has happened and that any attempt to do anything other than pay the requested ransom will result in the server destroying the user files. Like a digital version of a hostage situation, there is a countdown timer, a clear threat if demands are not made and limited options available to get out of it.
Andrew Weisskopf, senior systems analyst at IT Services Network and Communications, said the virus has been discussed for about a month among other higher-education institutions.
“For our [Iowa State’s] emailing systems, the attachments carrying the infections are being removed; other schools don’t do that,” Weisskopf said. “So far we’re seeing student machines being affected through accounts that aren’t Iowa State-related.
“The effects of the virus are really devastating. Unfortunately they did things right; they’re using public key cryptography, which makes decryption of infected machines mathematically infeasible.”
Users who paid the ransom have reported that their files were restored, Weisskopf said, but he pointed out “these are criminals we’re dealing with.”
“We’ve also had five students who have called the Solution Center for assistance,” Weisskopf said. “The general advice is to reformat and reinstall your computer, pretty much for any sort of malware infection.”
Weisskopf said the targets of the virus seem to be varied.
“I’ve seen reports of businesses receiving it, other colleges. … The method that it is targeting people who don’t back up their data,” he said. “At the moment for campus, we have it under control. It’s a constant vigilance.”
Most cyber criminals cover their tracks.
“It’s very hard to tell the origin of the virus; the server moves on a daily basis,” Weisskopf said. “Most attack groups, whether they’re foreign or domestic, they all are going through another system before they target you directly. The warning messages are very good English, unlike most phishing attempts.”
Weisskopf said Macs are unaffected by the virus but that students should still update their protection and backup software. For Windows users, Weisskopf said it would be possible to remove the virus by inducing a revert to a previous restore point, which brings the Windows machine to a previous state, along with all of the files on it.
Weisskopf recommended using systems like CyBox to back up files to multiple locations. Should a student’s computer be infected, the user is urged to not pay the $300 ransom; instead, students should call immediately IT Services’ departmental support staff or the Solution Center at 515-294-4000.